Cryptocurrency
Cryptocurrencies are digital tokens that built upon a decentralized ledger that allows for peer-to-peer transfer of value over the internet
What is Cryptocurrency?
A cryptocurrency is a type of digital asset that allows for one party to transfer value from one party to another over the internet without the use of a centralized entity, like a bank.

However, since the two parties might be previously unknown to one another, how can the receiving party be sure that the value of the token hasn’t already been used or that the sending party actually owns the token in the first place?
That’s why cryptocurrencies use a distributed blockchain that allows anyone to verify that the token is actually owned by the person who is sending it. The blockchain acts like a written ledger of every transaction conducted and is very difficult to change after anything has been written to it.
In order to preserve the integrity of the ledger, cryptocurrencies require consensus, or agreement, by a majority of users of that cryptocurrency before it can be added to the ledger. Different cryptocurrencies have different ways of achieving this consensus, as well as rewards for being the party chosen to add an entry to the ledger.
The most famous cryptocurrency is Bitcoin (BTC), followed by Ether, the native token for the Ethereum network. Any other crypto token besides those two is generally known as Altcoins now but originally was meant to refer to “Alternative to Bitcoin.”
Key Highlights
- A cryptocurrency is a type of digital asset that allows for one party to transfer value from one party to another over the internet without the use of a centralized entity, like a bank.
- Cryptocurrencies address the double spend problem by using digital signatures and hash functions to ensure that the receiver of a cryptocurrency coin or token hasn’t spent it yet and is the actual owner of the digital asset.
- There is a myriad of purposes that cryptocurrencies can serve, and more are being introduced as this nascent technology continues to be explored.
How Do Cryptocurrencies Work?
How do cryptocurrencies transfer value digitally between two trustless parties, then? It does so by combining two concepts of blockchain technology – digital signatures and hash functions – to create a tamper-proof trail of who owns what in order to avoid the double spend problem.
Double Spend Problem
Since cryptocurrencies are decentralized and digital, the key problem faced is how to prevent someone from making more digital copies of their digital tokens and spending it twice or even more times. This is called the Double Spend Problem.
This problem doesn’t exist with paper money because if the transaction is in cash, there is finality as once the recipient has the paper bill in their hands, the spender no longer has it, so they cannot double-spend with it.
Similarly, with a bank transfer, for example, once the money has been moved from the sender’s account into the recipient’s, the sender cannot take the money back without the recipient’s authorization. Bank transfers also require a centralized party to deduct the funds from the sender’s account and deposit them into the recipient’s. So there is no risk of double-spending in this case either.
Blockchains address that problem by having a tamper-resistant ledger of who owns what that anyone can verify without the need for a centralized intermediary.
Blockchains
A blockchain is simply a database of transactions, often called a distributed ledger, that has been duplicated and broadcast to a network of users, who can all verify and agree on the database.
Each new block, which in cryptocurrencies contains a list of transactions, that comes afterward is time-stamped and has to be approved by a network of computer servers, called nodes, each of whom checks its validity.
Consensus
Once every node has checked a block, there is a sort of electronic vote, as some nodes may think the transaction is valid, and others think it is a fraud. This is called consensus.
If a majority of nodes say that a block is valid, then it is written into the blockchain, literally chaining together a string of blocks. This newly accepted version of the blockchain ledger is broadcast over the entire network of nodes that run the same blockchain software. All the nodes have the same copy, and then the process repeats again to verify the next block to add to the chain.
Tamper-Resistant – Not Tamper-Proof
As more blocks are added, the transaction becomes increasingly difficult to reverse or alter, making the blockchain tamper-resistant but not tamper-proof.
Old blocks cannot be modified without also changing the data in subsequent blocks that follow it in the chain. Furthermore, all computers in the network must agree to change this old block. This is what prevents fraudulent data.
If a counterfeiter attempts to create a fake record of cryptocurrency, the computers in the network will disagree with the change in an old block. The fake record will be invalid and not recorded in the network.
Uses of Blockchains
Blockchains can also be used for a variety of purposes, such as issuing and maintaining real estate titles and records, medical record-keeping, tracking produce, livestock, and medicine throughout the supply chain, verifying ownership or validity of assets or rights, trade finance, and even voting mechanisms.
Digital Signatures
In order to verify who actually owns what, cryptocurrencies use the concept of digital signatures. A digital signature behaves like a handwritten signature to mark someone’s agreement to a document or transaction or to prove their identity.
Key Pairs
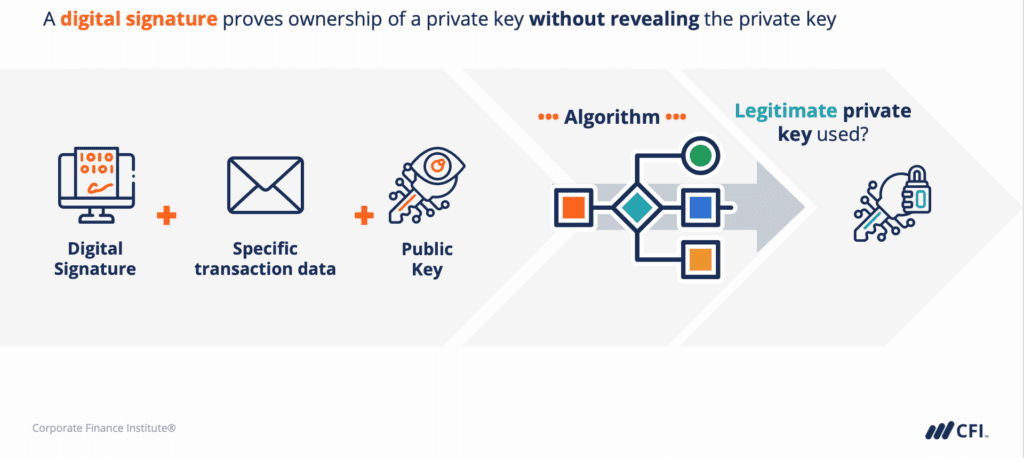
Cryptocurrencies employ digital signatures that consist of two related keys, a private key and a public key. This “key pair” are used together to encrypt and decrypt transactions. The public key can be thought of as the identity of the owner, and the private key can be thought of as secret information that allows the owner to prove their ownership of the public key.
A digital signature is something that you can use to show that you know the private key connected to a public key without having to reveal the actual key, so if anyone needs you to prove that you have the private key for any specific public key, you can prove it by supplying a digital signature.
By using the correct digital signature with the specific data of your cryptocurrency transaction together with your public key, anyone can run it through a specific algorithm to confirm whether a legitimate private key was used to create that digital signature WITHOUT giving away your private key.
This pair of keys basically allows one key to validate what the other key does to prove legitimacy.
Hash Functions in Cryptocurrency
What is a Hash Function?
A hash function is a mathematical function that converts any digital data into an output string with a fixed number of characters. Hashing is the one-way act of converting the data (called a message) into the output (called the hash).
Hashing is useful to ensure the authenticity of a piece of data and that it has not been tampered with since even a small change in the message will create an entirely different hash.
Bitcoin’s Proof-of-Work Protocol
The most famous cryptocurrency, Bitcoin, uses hash functions in its blockchain. Powerful computers, called miners, race each other in brute force searches to try to solve hashes in order to earn the mining rewards of new Bitcoins, as well as processing fees that users pay to record their transactions on the blockchain.
NONCE
Solving a hash involves computing a proof-of-work, called a NONCE, or “number used once,” that, when added to the block, causes the block’s hash to begin with a certain number of zeroes. Once a valid proof-of-work is discovered, the block is considered valid and can be added to the blockchain.
Since each block’s hash is created by a cryptographic algorithm – Bitcoin uses the SHA-256 algorithm – the only way to find a valid proof-of-work is to run guesses through the algorithm until the right number is found that creates a hash that starts with the right number of zeroes. This is what Bitcoin miners are doing, running numbers through a cryptographic algorithm until they guess the valid NONCE.
Putting It All Together – Bitcoin Example
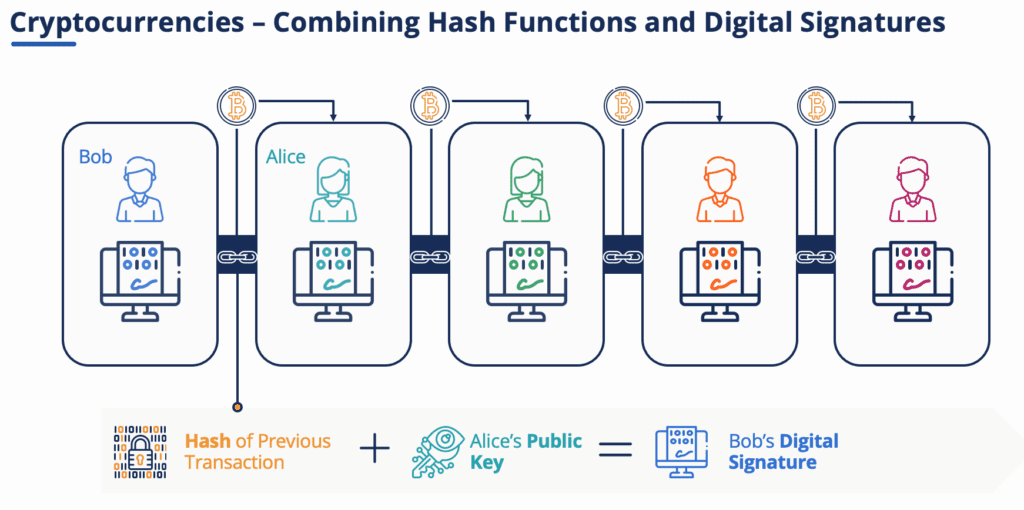
Cryptocurrencies work by combining hash functions and digital signatures. For example, a Bitcoin owner who wishes to transfer ownership of the coin to someone starts by digitally signing a hash of the transaction and the public key of the next owner and broadcasting the signed transaction to all nodes adding that to the end of the blockchain.
Anyone can verify the validity of the signature using public keys and, thus, the validity of the transaction.
The recipient of the Bitcoin can easily check the signatures to verify the chain of ownership. However, being a decentralized ledger, the problem is that the payee cannot verify that the previous owner didn’t already spend the coin.
The solution is to use time-stamping and hash functions to validate the block in question. Basically, a hash is created for each block based on the hash of the previous block, the transactions that make up the block, and proof of work.
This ensures that changing any part of a block completely changes its associated hash, the proof-of-work required to solve the hash, and the hash of all subsequent blocks. This requires a lot of computing power, over 50% of the computing power of all the users of Bitcoin, which makes it extremely expensive and difficult to accomplish.
Coins versus Tokens
You may hear the term “coin” and “token” used interchangeably, but technically, that is not true. Coins are cryptocurrencies that have their own blockchain. So, for example, Ether is the native token for the Ethereum blockchain network, so it would be a coin.
A token, on the other hand, is a cryptocurrency that doesn’t have its own blockchain and instead runs on another blockchain. Hence, any token that is developed following the rules outlined in Ethereum’s ERC20 smart contract standard and runs on Ethereum’s blockchain other than Ether is considered a token. A prime example is Tether, which not only runs on the Ethereum network but also on other blockchains.
Types of Cryptocurrencies
There are thousands[1] of cryptocurrencies out there, with hundreds being introduced daily, so it can be confusing to categorize. However, there are generally four types of cryptocurrencies out there.
What about NFTs?
NFT is an acronym for Non-Fungible Token, a special type of cryptocurrency that is highly unique that is commonly used to prove ownership and authenticity for an underlying asset, digital or physical. NFTs are a form of digital signature that is publicly verifiable because it is stored on a blockchain. Learn more here.
How Do You Hold Cryptocurrencies?
While you might be familiar with a physical wallet that we keep in our pocket or purse that holds our paper money or coins, when it comes to cryptocurrencies, you will need a cryptocurrency wallet.
How to Obtain Cryptocurrency?
While it is certainly possible to sell goods or services in exchange for cryptocurrency, for most people, the easiest way to get cryptocurrency is to buy it, either from an exchange or another user.
You may also obtain cryptocurrencies from an initial offering, called an ICO.
Some cryptocurrencies allow you to mine or stake new coins in return for helping to ensure the integrity of the system.
Lastly, you can also create your own cryptocurrency from scratch.
Learn More
Thank you for reading CFI’s guide to Cryptocurrencies. To keep learning and developing your knowledge base, please explore the additional relevant resources below:
- How to Buy Cryptocurrency
- Altcoin Guide
- What is the Best Time to Buy Cryptocurrency
- How to Trade Cryptocurrency
- See all cryptocurrency resources
Article Sources

Create a free account to unlock this Template
Access and download collection of free Templates to help power your productivity and performance.
Already have an account? Log in
Supercharge your skills with Premium Templates
Take your learning and productivity to the next level with our Premium Templates.
Upgrading to a paid membership gives you access to our extensive collection of plug-and-play Templates designed to power your performance—as well as CFI's full course catalog and accredited Certification Programs.
Already have a Self-Study or Full-Immersion membership? Log in
Access Exclusive Templates
Gain unlimited access to more than 250 productivity Templates, CFI's full course catalog and accredited Certification Programs, hundreds of resources, expert reviews and support, the chance to work with real-world finance and research tools, and more.
Already have a Full-Immersion membership? Log in